| << Chapter < Page | Chapter >> Page > |
It is also useful to set only one of the rotation angles to a non-zero value and watch the rotation around a line parallel to that axis take place.
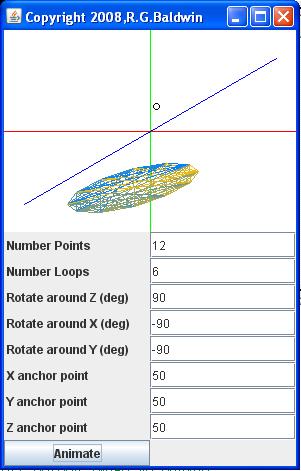
A stop-action screen shot
Figure 4 shows a screen shot of the disk in motion somewhere between the beginning and the end of its very complex trajectory forone particular set of rotation and anchor point parameters.
Figure 4 Screen shot of the graphic output from StringArt04.
Exercises
I will also provide exercises for you to complete on your own at the end of the module. The exercises will concentrate on the material that you have learnedin this and previous modules.
The game-math library named GM01 has not been modified since I presented and explained it in an earlier module titled GAME 2302-0135: Venturing into a 3D World . A copy of the source code for the library is provided in Listing 30 for your convenience. Since Ihave explained the code in the library in earlier modules, I won't repeat those explanations here.
A link to a zip file containing documentation for the library was provided in the earlier module.
This is an interactive 3D game program. In fact, this is the first game program that I have presented in this collection on game math. This gamesimulates a school of prey fish being attacked and eaten by a predator. The objective for the player is to cause the predator to eat all of the prey fish ina minimum amount of time. Although the story line of the game is rather simple, the math involved is not simple at all.
Player initiates attacks
The player in this game initiates a series of attacks by the predator by clicking the Attack button shown in Figure 5 . The winning strategy for the player is to time the attacks in such a way as to minimize the elapsed timerequired for the predator to eat all of the prey fish. The final elapsed time depends on both strategy and chance. In other words, as is the case in manygames, this game is part strategy and part chance.
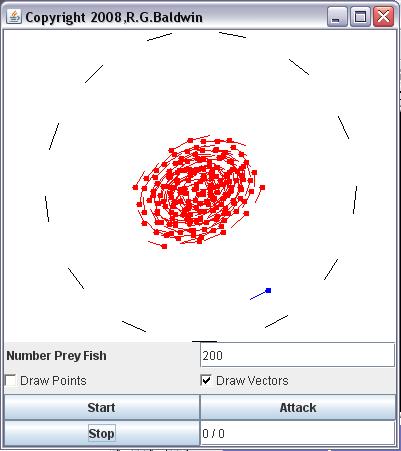
A swirling cluster of prey fish
The prey fish, (shown in red) , tend to swim in a large swirling cluster as shown in Figure 5 when they aren't being harassed by the predator.
Figure 5 Prey fish in a large swirling cluster.
Predator behavior
The predator, (shown in blue in Figure 5 ) , swims around the cluster, darting into and through the cluster when the user clicks the Attack button. During an attack, the predator attempts to eat as many prey fish aspossible. When the predator attacks, the prey fish tend to scatter (as shown in Figure 1 ) , breaking up their tight formation and making it more difficult for the predator to catch them. If the predator is allowed to swim around themagain for a short period following an attack, they will form back into a cluster.
Proper timing is important
The attacks should be timed so that the prey fish are in a reasonably tight cluster at the beginning of each attack so that multiple prey fish will be eatenduring the attack. However, allowing too much time between attacks is detrimental because it increases the total elapsed time. Thus, the player mustmake a tradeoff between elapsed time between attacks and the tightness of the cluster at the beginning of each attack. Another disadvantage of waiting too long between attacks will be explained later.

Notification Switch
Would you like to follow the 'Game 2302 - mathematical applications for game development' conversation and receive update notifications?